List Categories and Listings by I
Patch for Endpoint Manager can swiftly detect missing patches in Windows, Mac OS, Linux, and hundreds of third-party apps (Acrobat Flash/Reader, Java, Web browsers, and more) and deploy expertly pre-tested patches everywhere you need them. Patch for Endp ...
Incapsula cloud-based web application firewall (WAF) is a managed service that protects from application layer attacks, including all OWASP top 10 and even zero-day threats. Incapsula CDN is a gateway for all incoming traffic to your web application. Thi ...
Infer is a static analysis tool - if you give Infer some Java or C/C++/Objective-C code it produces a list of potential bugs. Anyone can use Infer to intercept critical bugs before they have shipped to users, and help prevent crashes or poor performance.
Imperva Web Application Firewall analyses traffic to your applications to stop web application attacks. Imperva WAF provides PCI-compliant and automated security that integrates analytics to go beyond OWASP Top 10 coverage, and reduces the risks cre ...
Prepare every employee with phishing simulations and training Stop dreading the day a phishing attack slips past your cyber defenses. Get the peace of mind from knowing your employees are prepared if it happens. Choose from 1,000+ realistic phishing tem ...
Code42 Incydr is a SaaS data risk detection tool that locates and mitigates insider threats without disrupting regular operations. It monitors and documents how employees use and share data between their computers and cloud services. All user activity is ...
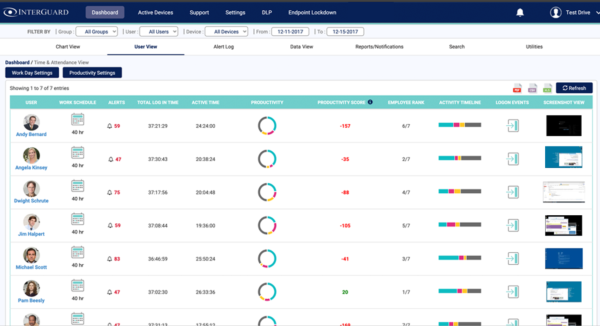
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
Features: Intelligent insights across environments - provides visibility and applies context to on-prem and cloud-based resources; leverages continuous monitoring for a zero trust approach to security. Built-in analytics to accurately detect threats - ...
Easy to use and fast to deploy Privileged Access Management (PAM) available both on-premises or in the cloud. IBM Security Verify Privilege Vault makes it easy to identify and secure all service, application, administrator, and root accounts across your ...
Built and vetted by expertsInsightIDR has internal and external threat intel for our post-perimeter era, and the world’s most used penetration testing framework Metasploit. We do relentless research with Projects Sonar and Heisenberg. And because “we drin ...
The main goal of this conference is to promote research on all aspects of network security and cryptology.
This multi-purpose Firewall readies you for the future through Deep Packet Inspection, unique multi-platform support, and market-leading IPSec VPN support. Its unparalleled network monitoring turns you into an security professional with unique real-time i ...
Complete "Deep Packet Inspection" Security Provides unprecedented broad-scoped security and enables the network administrator to effortlessly eliminate (D)DoS attacks, trojans, worms, SYN floods, ICMP floods, port-scanning, e-borne viruses, executable e-m ...
PFilter is a software package that can be used to provide network address translation (NAT) or firewall services. To use, it can either be used as a loadable kernel module or incorporated into your UNIX kernel; use as a loadable kernel module where possib ...
Transparent, standards-based cross-platform unified IPSec technology, extends the InJoy Firewall? with capability of building VPN's and secure channels ? allowing corporations to deploy it either as a VPN Gateway or as a secure VPN Client.
The Innominate mGuard products offer extensive security functions such as VPNs (Virtual Private Networks), firewall and optional virus protection (powered by Kaspersky) ? regardless of the computer platform used. With the Innominate Security Configuration ...
IP-Granite is capable of securing all your information travelling over the Intranet or the Internet. Making use of the widely respected IPSec protocol, IP-Granite authenticates users, servers and gateways to one another, encrypting all communication flowi ...
Ingate SIParator / Firewall Popular
The Ingate SIParator / Firewall SBC RTS-FW The Ingate SIParator is a powerful, flexible and cost-effective Enterprise Session Border Controller (E-SBC) for SIP connectivity, security and interoperability, such as connecting PBXs and Unified Communication ...
east-tec InvisibleSecrets is a steganography and file encryption software that allows you to encrypt file and folder structures that contain confidential data and hide files, making it completely invisible to any user. Other useful features include: Powe ...
IDA Pro as a disassembler is capable of creating maps of their execution to show the binary instructions that are actually executed by the processor in a symbolic representation (assembly language). Advanced techniques have been implemented into IDA Pro s ...