List Categories and Listings by D
DEV522: Defending Web Applications Security Essentials is intended for anyone tasked with implementing, managing, or protecting Web applications. It is particularly well suited to application security analysts, developers, application architects, pen test ...
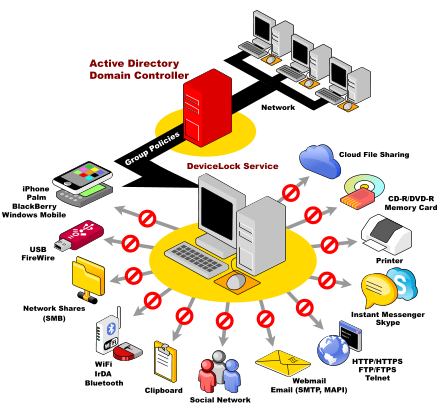
DeviceLock DLP Suite consists of five modules that protect your organization from data leak threats: DeviceLock provides network administrators the ability to set and enforce contextual policies for how, when, where to, and by whom data can or can&rsqu ...
Organised by the DFN-CERT (German Research Network). Mainly held in German with some international speakers. Visitors range from academic background, industry, civil government and Defence. Usually around mid March.
DirX Identity offers an extensive identity management solution for enterprises and organizations. It gives the right people the right access to the right resources at the right time and thus leads to productivity, information security, a perceptible reduc ...
DirX Audit provides a platform for the central collection, normalization, storage, and analysis of audit trails from different audit sources. Auditors can use DirX Audit's web-based user interface to analyze and correlate the audit logs in the central ...