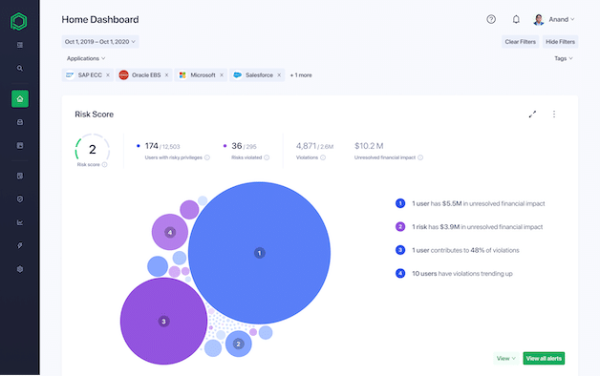
List Categories and Listings by P
The Certified Penetration Testing Consultant course is designed for IT Security Professionals and IT Network Administrators who are interested in taking an in-depth look into specific penetration testing techniques used against operating systems. This cou ...
Protect against data loss at the endpoint Proofpoint Endpoint Data Loss Prevention (DLP) takes a modern, people-centric approach to protecting your data. It provides you with integrate content awareness and behavioural and threat awareness. This gives yo ...
Pathlock Control is a comprehensive insider threat management solution that can detect, automatically react to, and proactively prevent insider threats within your most critical business applications. It seamlessly integrates with more than 140 systems in ...
Tighten security with Firewall as a Service Legacy firewalls can protect the company’s internal perimeter, but they can’t ensure its safety across hybrid clouds. Perimeter 81's Firewall as a Service ensures that only authorized users can connect to your ...
PhishingBox's Phishing Simulator allows organisations to target any employee or group of employees with a simulated spear phishing attack to test their security awareness. The phishing simulator includes a library of templates which are designed to mimic ...
The Phished security awareness training platform combines automated phishing simulations with interactive cybersecurity education and threat intelligence. Fully Automated Phishing Simulations AI-driven phishing simulations are based on individua ...
Positive Technologies Application Firewall (PT AF) is a modern response to the constantly evolving web threat landscape. It combines real-time analytics, innovative technologies, and proven approaches to deliver proactive and continuous protection of all ...
Polyspace®static code analysis products use formal methods to prove the absence of critical run-time errors under all possible control flows and data flows. They include checkers for coding rules, security vulnerabilities, code metrics, and hundreds of ad ...
Parasoft Jtest enables you to accelerate Java software development while minimizing risks introduced into the code, by providing comprehensive analysis, guidance, and tools to get the job done. Jtest integrates with Parasoft DTP for sophisticated reportin ...
ProxyStrike is an active Web Application Proxy. It's a tool designed to find vulnerabilities while browsing an application. It was created because the problems we faced in the pentests of web applications that depends heavily on Javascript, not many web s ...
Deliver C and C++ software that’s robust, predictable, and secure. Manage risk and costs by building better software. Static analysis and unit testing are critical for application quality, security, and safety, and the cornerstone of any connected-applic ...
Pylint is a source code, bug and quality checker for the Python programming language. It follows the style recommended by PEP 8, the Python style guide.
PC-Lint Plus is a comprehensive static analysis solution for C and C++. Comply with Safety Standards Enforce compliance with industry coding standards including MISRA, AUTOSTAR, and CERT C, customise detection of individual guidelines and easily s ...
Patch Manager Plus is an all-around patching solution, offering automated patch deployment for Windows, macOS, and Linux endpoints, along with patching support for 950+ third-party updates across 850+ third party applications. It's available both on-premi ...
Phishing Frenzy is an Open Source Ruby on Rails application that is leveraged by penetration testers to manage email phishing campaigns. The goal of the project is to streamline the phishing process while still providing clients the best realistic phishi ...
A tool to collect DNS records passively to aid Incident handling, Network Security Monitoring (NSM) and general digital forensics. PassiveDNS sniffs traffic from an interface or reads a pcap-file and outputs the DNS-server answers to a log file. Passive ...
Pompem is an open source tool, which is designed to automate the search for exploits in major databases. Developed in Python, has a system of advanced search, thus facilitating the work of pentesters and ethical hackers. In its current version, performs s ...
Pig or (Packet intruder generator) is a Linux based packet crafting tool. You can use Pig for a number of different purposes such as testing your IDS/IPS through to spoofing ARP. Pig brings with it a number of well-known attack signatures which are ready ...
Keep this life-saving tool handy to recover forgotten passwords quickly whenever needed. Key Benefits 7 password recovery modules for MS Word, Excel, Windows, Outlook Express, and more, combined in one tool Instantly previews password-protected MS Wo ...
Research in pervasive computing continues to gain momentum. The importance of security and privacy in a pervasive computing environment cannot be underestimated. As in previous years, PerSec will bring together the world's experts on this topic and provid ...