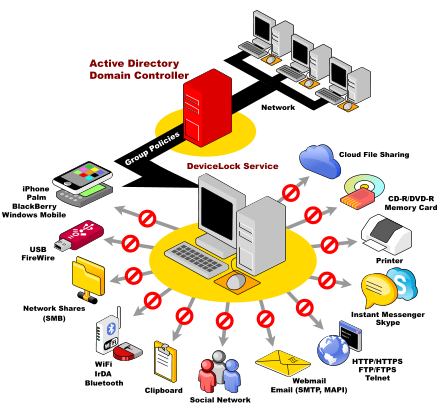
In today's age of small, portable storage devices, the risk introduced into the network by these devices is large. Trojans and viruses can be brought in on them, defeating nearly all of the network-based anti-virus measures implemented. At the same time these storage devices can be used to carry out sensitive data, compromising the business. Even when used legitimately to port information, they are easily laid down and lost, making that information available to anyone who picks up the device.
Endpoint Security includes applications to control the use of portable storage devices on the computer, encryption of the data on those devices, and improvements in the devices themselves to secure the information on them.
Disk EncryptionIncreased remote working makes it more important than ever to secure computers and the data on them. With the huge number of laptops lost, stolen, or misplaced every day, a crucial first line of defense against the loss or theft of devices ...
Safend Protector prevents internal/external data leakage by monitoring endpoint devices and data flow. Using granular and customizable security policies and rules, Protector automatically detects, permits and restricts files and encrypts media devices. Ve ...
AppSense Environment Manager provides consistent and contextual user environments across multiple application delivery mechanisms. With AppSense Environment Manager, IT can manage user profiles with minimal maintenance as well as provide users with some l ...
Becrypt have worked closely with the UK National Cyber Security Centre (NCSC) to support the enhanced security characteristics of NCSC’s Advanced Mobile Solutions program, resulting in the first MDM platform that can support dynamic Deep Packet Inspection ...
DeviceLock DLP Suite consists of five modules that protect your organization from data leak threats: DeviceLock provides network administrators the ability to set and enforce contextual policies for how, when, where to, and by whom data can or can&rsqu ...
You manage hundreds or thousands of devices and applications, numerous assets, and an unending list of software patches. And on top of it all, your workforce is constantly changing with new requests every day. The ZENworks Suite can help. ZENworks Servic ...
Continually tracking your network’s endpoints, Safend Auditor silently pinpoints all usage of USB, FireWire, PCMCIA, PCI, internal storage and WiFi connections. Displaying complex information comprehensively, Auditor reports can be exported and manipulat ...
Discover and protect sensitive data on premises and in the cloud. Identify Business Critical DataClassify structured and unstructured data with exact data matching and over 300 content types. Get Powerful ReportingCreate reports on demand or schedule fo ...
McAfee Application Control software provides an effective way to block unauthorized applications and code on servers, corporate desktops, and fixed-function devices. This centrally managed whitelisting solution uses a dynamic trust model and innovative se ...
McAfee Endpoint Protection — Advanced Suite delivers integrated, proactive security that blocks malware and zero-day threats. It protects Windows, Mac, and Linux systems on and off your network. With centralized policy-based management and auditing, Endpo ...
BeyondTrust Privilege Management elevates privileges to known, trusted applications that require them, controls application usage, and logs and reports on privileged activities using security tools already in place. Provide users enough endpoint privileg ...
Enjoy the freedom and flexibility of remote working with the peace of mind that your files will remain safe on your secure USB, even in the event of loss or theft with the SafeToGo® Solo. Prevent unauthorised access – with the device’s AES 256-bit XTS en ...
Data protection does not have to get in the way of business productivity. Forcepoint’s focus on unified policies, user risk, and automation makes data security frictionless and intuitive. Control all your data with one single policyReplace broad, sweepin ...
Safend Reporter automatically generates reports on intentional and unintentional misuse of private company information. Reports can be strategic and periodic and built-in or customized by an administrator. Each report is set in a comprehensive interface a ...
Endpoint Central (formerly Desktop Central) is a unified endpoint management and security solution that helps in managing servers, laptops, desktops, smartphones, and tablets from a central location. It's a modern take on desktop management that can be sc ...