Tags: Network
The SecurityTube Wi-Fi Security Expert (SWSE) is an online certification for Wi-Fi Security and Penetration Testing. This course is ideal for penetration testers, security enthusiasts and network administrators. The course leading to the certification exa ...
The vBroker Series provides you with flexible yet advanced network visibility by accessing, optimizing, and delivering traffic from multiple networks to multiple network monitoring and security tools – both passive and active (inline). Featuring both fix ...
Safeguard your sensitive company data. Blue Coat Data Loss Prevention (DLP) enables you to detect and block potential data leaks quickly and accurately, all while achieving industry and regulatory compliance. With Blue Coat DLP, you can leverage powerful ...
Zscaler Data Loss Prevention protects your confidential information and intellectual property by inspecting all of your outbound Internet traffic, including SSL-encrypted traffic, and helps you meet industry, statutory and regulatory compliance standards ...
BUFFERZONE is a virtual container that protects any content source that you define as potentially insecure including web browsers, email, Skype, FTP and even removable storage. You are able to definite granular containment poloicies according to network s ...
Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data on your computer. Running your Web Browser under the protection of Sandboxie means that all malicous software downloaded by the ...
Open-source wardriving app to netstumble, display and map found wireless networks and cell towers anywhere in the world, easily uploading to the http://wigle.net database. WiGLE was started in 2001 and now has over 150 million wifi networks worldwide. ...
Wifi Analyzer is a free Android app you can use for finding APs on your Android-based smartphone or tablet. It lists the basic details for APs on the 2.4-GHz band, and on supported devices on the 5-GHz band as well. You can export the AP list (in XML form ...
Vistumbler is an open source Windows application that finds Wireless access points - Uses the Vista command 'netsh wlan show networks mode=bssid' to get wireless information. It displays the basic AP details, including the exact authentication and e ...
Network Security Analysis Tool is a robust scanner which is designed for: Different kinds of wide-ranging scans, keeping stable for days Scanning on multi-user boxes (local stealth and non-priority scanning options) Professional-grade penetration tes ...
FOR572: Advanced Network Forensics and Analysis, was built from the ground up to cover the most critical skills needed to mount efficient and effective post-incident response investigations. It focuses on the knowledge necessary to expand the forensic min ...
The fully assembled and enclosed brother to the Throwing Star LAN Tap Kit. The pro model sports all of the same 10BASET and 100BASETX monitoring goodness ready to go in your kit bag, no soldering necessary. To a target network this little guy looks just ...
nTAPs are passive, full-duplex devices, offering complete visibility to monitoring devices regardless of traffic level. They work with the leading management tools for quick and easy deployment. nTAPs are transparent for monitoring critical links, and pro ...
EtherApe is a graphical network monitor for Unix modeled after etherman. Featuring link layer, IP and TCP modes, it displays network activity graphically. Hosts and links change in size with traffic. Color coded protocols display. It supports Ethernet, F ...
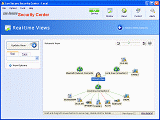
Security Center network access protection software designed to provide real-time network security monitor for intrusion detection IDS and prevention IPS that helps to protect networks from being vulnerable to unauthorized network connections, malicious ne ...
Wireless Protector is windows software that automatically disables wireless 802.11 / Broadband devices on computers that connected to the network LAN and re-enable the devices when the LAN cable is disconnected from the protected compu ...
Continually tracking your network’s endpoints, Safend Auditor silently pinpoints all usage of USB, FireWire, PCMCIA, PCI, internal storage and WiFi connections. Displaying complex information comprehensively, Auditor reports can be exported and manipulat ...
The most comprehensive visibilityGet 100% visibility of all devices connected to your extended networks, in real time, due to our 20+ active and passive techniques. Zero Trust for all connecting devicesContain breach impact through continuous agentless m ...