Kelsey Chalmers
This training course is a series of educational interactive training sessions where the attendees will gain hands-on experience. They will be able to identify security flaws in web applications customised or built for the training course. They will also b ...
Gigabit Data Diodes are fully hardware based ensuring unidirectional transmission without any possibility of data slowing in the reverse direction. They provide an absolute defence against a broad range of external, cross domain and insider cyber threats ...
Simulate Email Threats Teach your users to identify and respond to potential security risks. Select from a selection of real-world threat templates, taken directly from Barracuda’s threat database, and expose your users to the latest email thre ...
The Phished security awareness training platform combines automated phishing simulations with interactive cybersecurity education and threat intelligence. Fully Automated Phishing Simulations AI-driven phishing simulations are based on individua ...
PhishingBox's Phishing Simulator allows organisations to target any employee or group of employees with a simulated spear phishing attack to test their security awareness. The phishing simulator includes a library of templates which are designed to mimic ...
FortiGate Next-Generation Firewalls deliver enterprise security at any scale with full visibility and threat protection. Organisations can weave security into the hybrid IT architecture and build security-driven networks to achieve: Ultra-fast security ...
Phishing Training Designed for People. Built for Enterprise. Cognitive automation enables individual learning paths that motivate people to recognize and report real attacks. 90% of breaches start with email. Focus your training where it's needed most. ...
Prepare every employee with phishing simulations and training Stop dreading the day a phishing attack slips past your cyber defenses. Get the peace of mind from knowing your employees are prepared if it happens. Choose from 1,000+ realistic phishing tem ...
King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. It features an easy to use, yet very flexible architecture allowing full control over both emails and server content. King Phisher can be used to ru ...
One-way data transfer with optical isolation for uncompromising network security & protection Create boundaries between trusted & untrusted networks by creating a physically secure one-way communication channel. Send data from one secure network ...
4Secure offers a flexible line of data diode cyber security products. Customers can choose from the appropriate hardware platform, which includes a base software package, and then select optional add-on software modules (at an additional cost) to meet the ...
Baseline Testing Baseline testing to assess the Phish-prone percentage through a simulated phishing attack. Train Your Users A large library of security awareness training content; including interactive modules, videos, games, posters and ...
M-Guard is an XML guard that is used at a network boundary to control traffic. An M-Guard instance is an application level data diode, with traffic flowing in one direction only. Commonly, M-Guard instances will be deployed in pairs, one controlling flow ...
VT AIR. The German Firewall VT AIR is the powerful enterprise firewall. The smart technology from Germany perfectly combines the advantages from the proven enterprise world with the undisputed advantages from the Linux world: VT AIR t ...
Overview FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. Organizations can weave security deep into the hybrid IT architecture and build security-driven networks to achiev ...
Forcepoint Next-Generation Firewall (NGFW) combines fast, flexible networking (SD-WAN and LAN) with industry-leading security to connect and protect people and the data they use throughout diverse, evolving enterprise networks. Forcepoint NGFW provides co ...
Tighten security with Firewall as a Service Legacy firewalls can protect the company’s internal perimeter, but they can’t ensure its safety across hybrid clouds. Perimeter 81's Firewall as a Service ensures that only authorized users can connect to your ...
Outsmart emerging threats in your digital business with industry-leading machine learning and behavioral modeling provided by Secure Network Analytics (formerly Stealthwatch). Know who is on the network and what they are doing using telemetry from your ne ...
Code42 Incydr is a SaaS data risk detection tool that locates and mitigates insider threats without disrupting regular operations. It monitors and documents how employees use and share data between their computers and cloud services. All user activity is ...
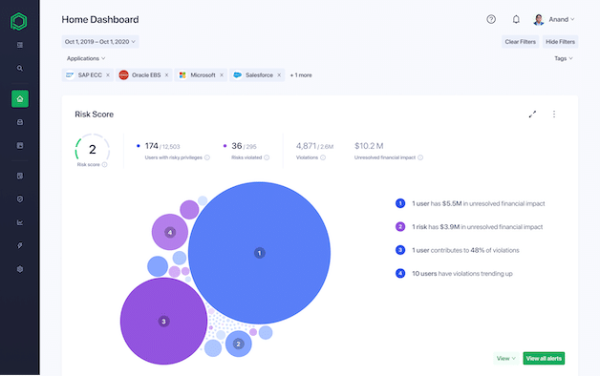
Pathlock Control is a comprehensive insider threat management solution that can detect, automatically react to, and proactively prevent insider threats within your most critical business applications. It seamlessly integrates with more than 140 systems in ...