Directory: Recently Added Listings
Powerful security for your online world, with convenience. 1 platform, 3 products to choose from. Whether you need to make managing your passwords a no-brainer, or share files securely with your team members, or keep hackers out of your life, we can make ...
Splunk Security Orchestration, Automation and Response (SOAR) Go from overwhelmed to in-control Automate manual tasks. Address every alert, every day. Establish repeatable procedures that allow security analysts to stop being reactive and focus on missi ...
Protect against data loss at the endpoint Proofpoint Endpoint Data Loss Prevention (DLP) takes a modern, people-centric approach to protecting your data. It provides you with integrate content awareness and behavioural and threat awareness. This gives yo ...
Integrated Data Loss Prevention (DLP) solution for enterprises. ManageEngine Endpoint DLP Plus is a dedicated DLP software designed to protect sensitive data on managed endpoint devices from data disclosure and theft by leveraging advanced data loss prev ...
Improve your security posture and quickly demonstrate compliance with a lightweight, ready-to-use, and affordable security information and event management solution. Identify and respond to threats faster Security Event Manager (SEM) will be another pai ...
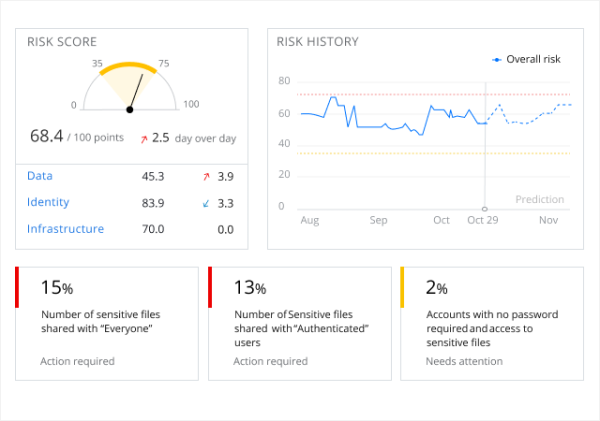
Netwrix analyzes user behavior, informing you of any deviations from the norm and mitigating risks related to sensitive data, regardless of its location. It smoothly integrates with Active Directory, Azure AD, Exchange, Office 365, and numerous other 3rd ...
ActivTrak is more than just an insider threat management solution. It gives you a zoomed-in perspective of what your employees actually do in their digital workspaces. For example, it monitors what applications they use and how they divide their time betw ...
Cerebral is an AI-powered security platform that integrates User & Entity Behavior Analytics (UEBA) with User Activity Monitoring (UAM), allowing rapid Data Breach Response (DBR). The ability to hunt threats by proactively recognizing signs of risk, l ...
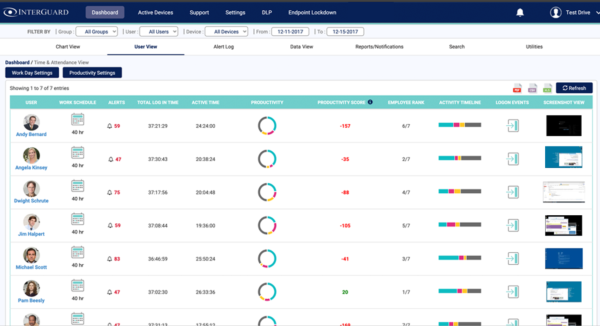
InterGuard’s employee monitoring software lets you track all employees activity from any endpoint - even when they work from home. Monitoring employee computer activity helps you proactively identify which employees are being productive and how much time ...
DARKBEAST provides incident responders, threat hunters, investigators, and intelligence analysts with a robust technology to dive into the cybercrime underground and investigate through KELA's cybercrime data lake. Gain visibility into underground operati ...
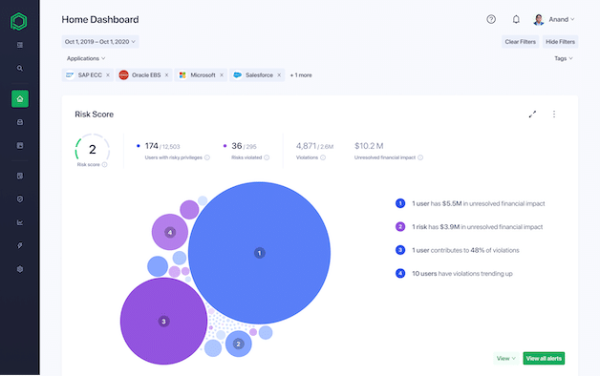
Pathlock Control is a comprehensive insider threat management solution that can detect, automatically react to, and proactively prevent insider threats within your most critical business applications. It seamlessly integrates with more than 140 systems in ...
Code42 Incydr is a SaaS data risk detection tool that locates and mitigates insider threats without disrupting regular operations. It monitors and documents how employees use and share data between their computers and cloud services. All user activity is ...
Outsmart emerging threats in your digital business with industry-leading machine learning and behavioral modeling provided by Secure Network Analytics (formerly Stealthwatch). Know who is on the network and what they are doing using telemetry from your ne ...
Tighten security with Firewall as a Service Legacy firewalls can protect the company’s internal perimeter, but they can’t ensure its safety across hybrid clouds. Perimeter 81's Firewall as a Service ensures that only authorized users can connect to your ...
Forcepoint Next-Generation Firewall (NGFW) combines fast, flexible networking (SD-WAN and LAN) with industry-leading security to connect and protect people and the data they use throughout diverse, evolving enterprise networks. Forcepoint NGFW provides co ...
Overview FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. Organizations can weave security deep into the hybrid IT architecture and build security-driven networks to achiev ...
VT AIR. The German Firewall VT AIR is the powerful enterprise firewall. The smart technology from Germany perfectly combines the advantages from the proven enterprise world with the undisputed advantages from the Linux world: VT AIR t ...
M-Guard is an XML guard that is used at a network boundary to control traffic. An M-Guard instance is an application level data diode, with traffic flowing in one direction only. Commonly, M-Guard instances will be deployed in pairs, one controlling flow ...
Gigabit Data Diodes are fully hardware based ensuring unidirectional transmission without any possibility of data slowing in the reverse direction. They provide an absolute defence against a broad range of external, cross domain and insider cyber threats ...
4Secure offers a flexible line of data diode cyber security products. Customers can choose from the appropriate hardware platform, which includes a base software package, and then select optional add-on software modules (at an additional cost) to meet the ...